Setting up Two-Factor Authentication (2FA)
Overview
Two-Factor Authentication (2FA) is a crucial security measure that adds an extra layer of protection to your Quiq account. 2FA is a security best practice that significantly enhances account security by requiring users to provide two different authentication factors to verify their identity, making it much harder for unauthorized users to gain access to accounts.
Quiq requires all accounts using Quiq as their identity provider (IdP) to have 2FA enabled.If you manage user sign-ins & accounts through Salesforce, Oracle, Dynamics, or a non Quiq IdP, 2FA in Quiq is not required.
Proactively Enabling Two-Factor Authentication
Admins can proactively enable 2FA for themselves and for their organization if they'd like. Navigate to the Security section within Admin, and scroll down to the Two-Factor Authentication section:
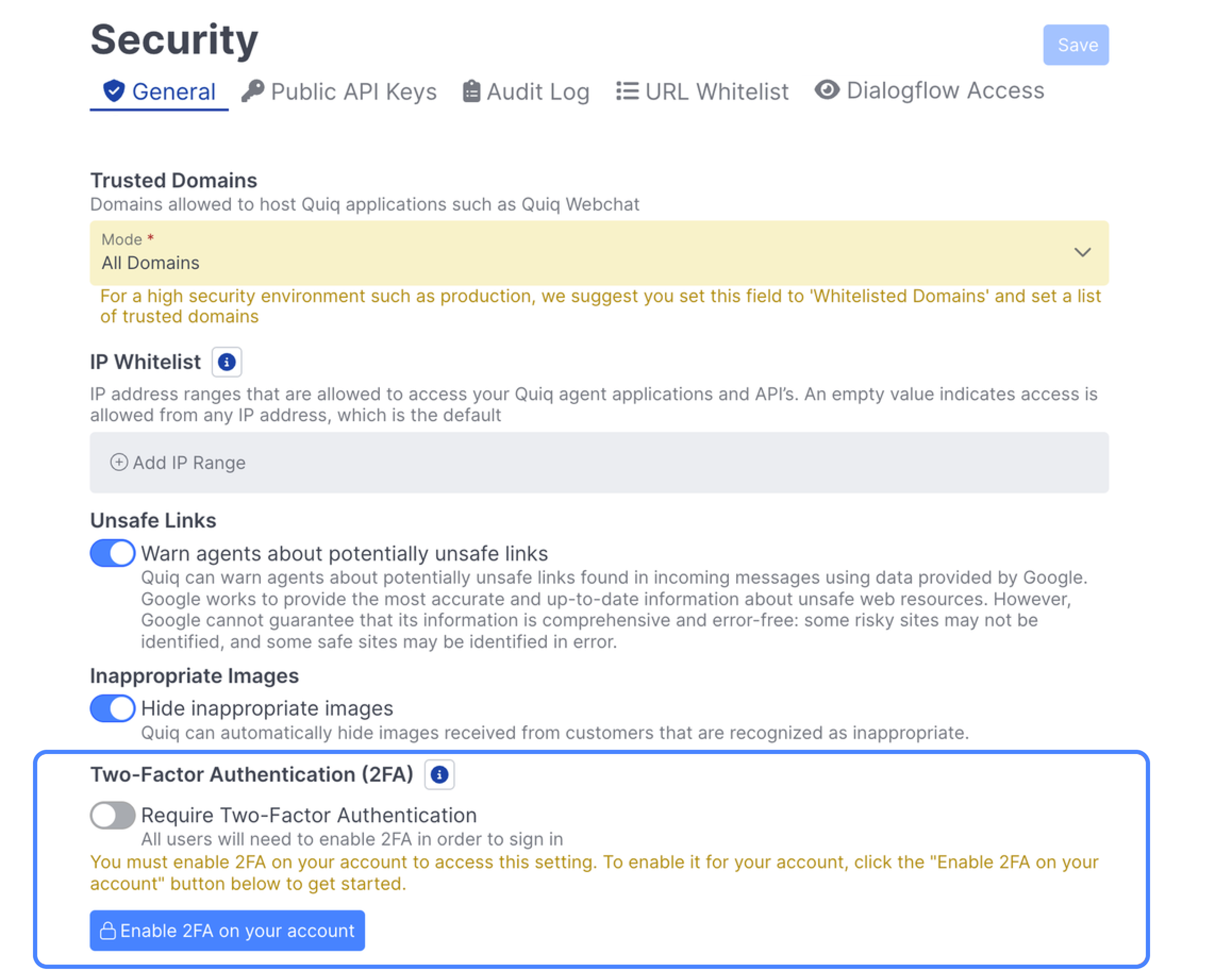
Enabling 2FA on your account
Below you'll find instructions for how to enable 2FA on your account for both Admins and Agents. For Admins, this is a necessary pre-requisite for enabling 2FA for your organization.
For Agents & Admins
Both Agents and Admins can enable 2FA on their accounts by navigating to the Security section for their account under User Settings. Below you'll find a guided demo walkthrough through the process:
For Admins
Admins can also enable 2FA directly from the Security page if they haven't already:
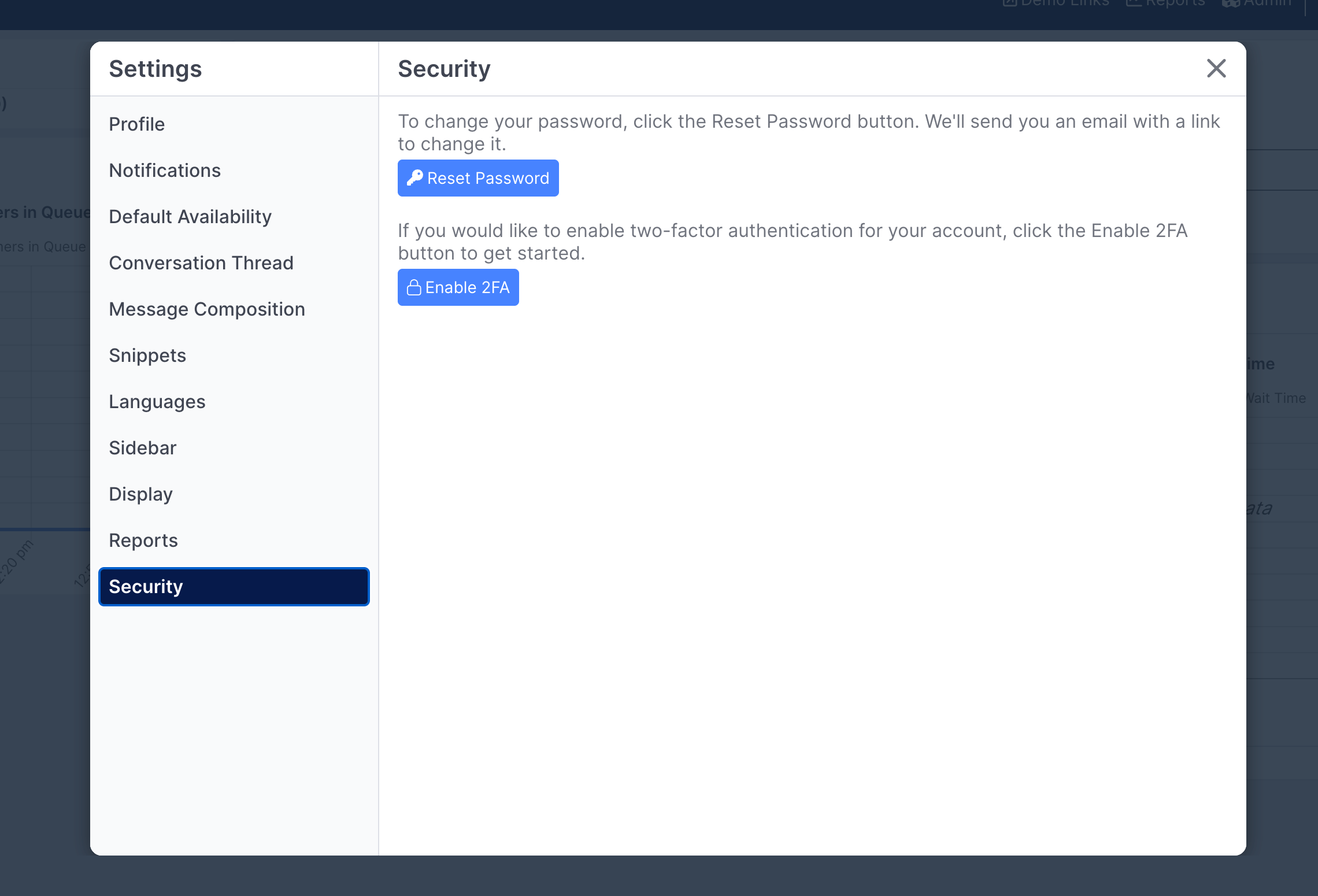
When you click the Enable 2FA button Quiq will send a code to the email associated with your user. Once you receive the email, enter that code in Step 2:
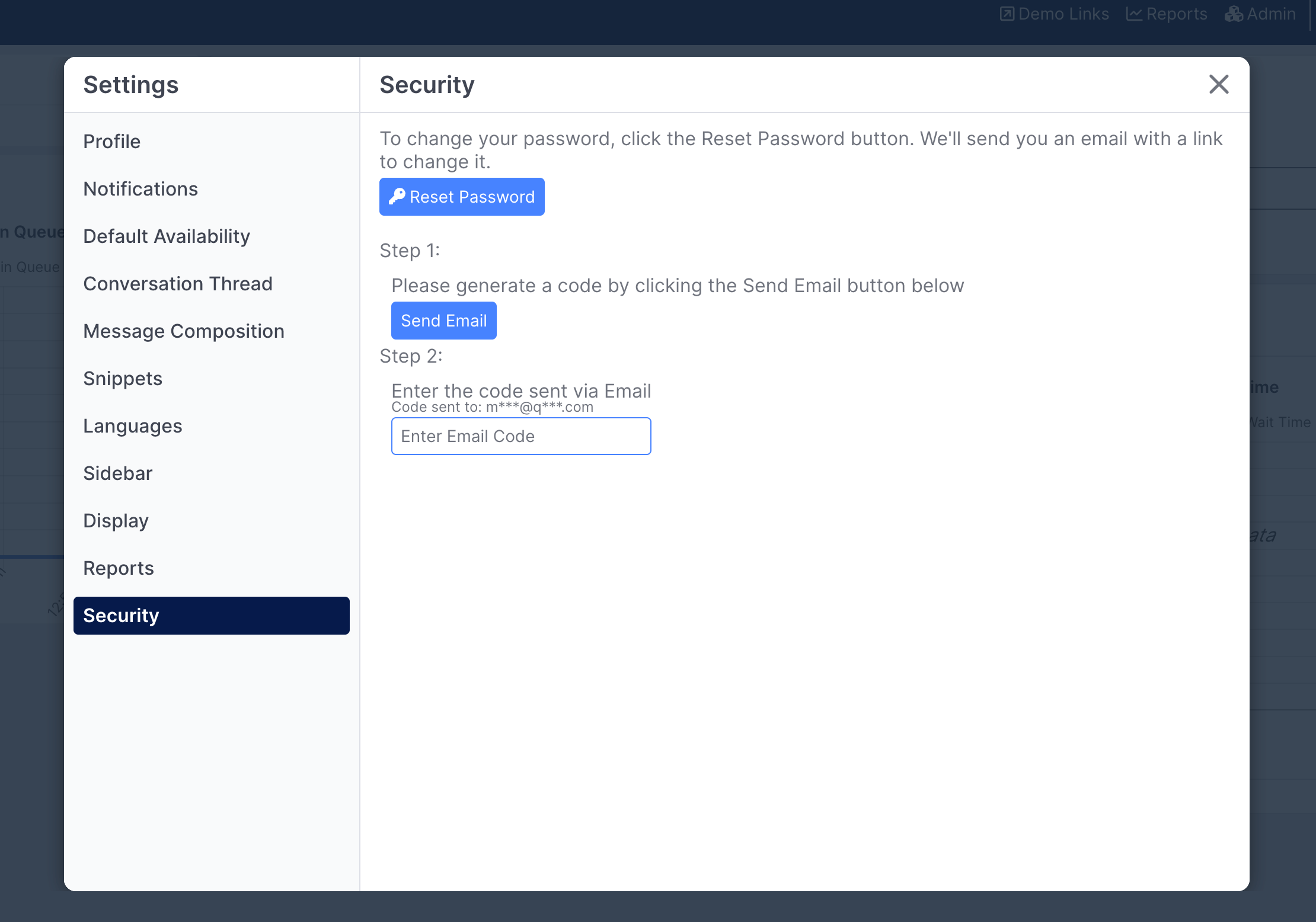
From there, you'll be prompted to scan the code with your preferred authentication app:
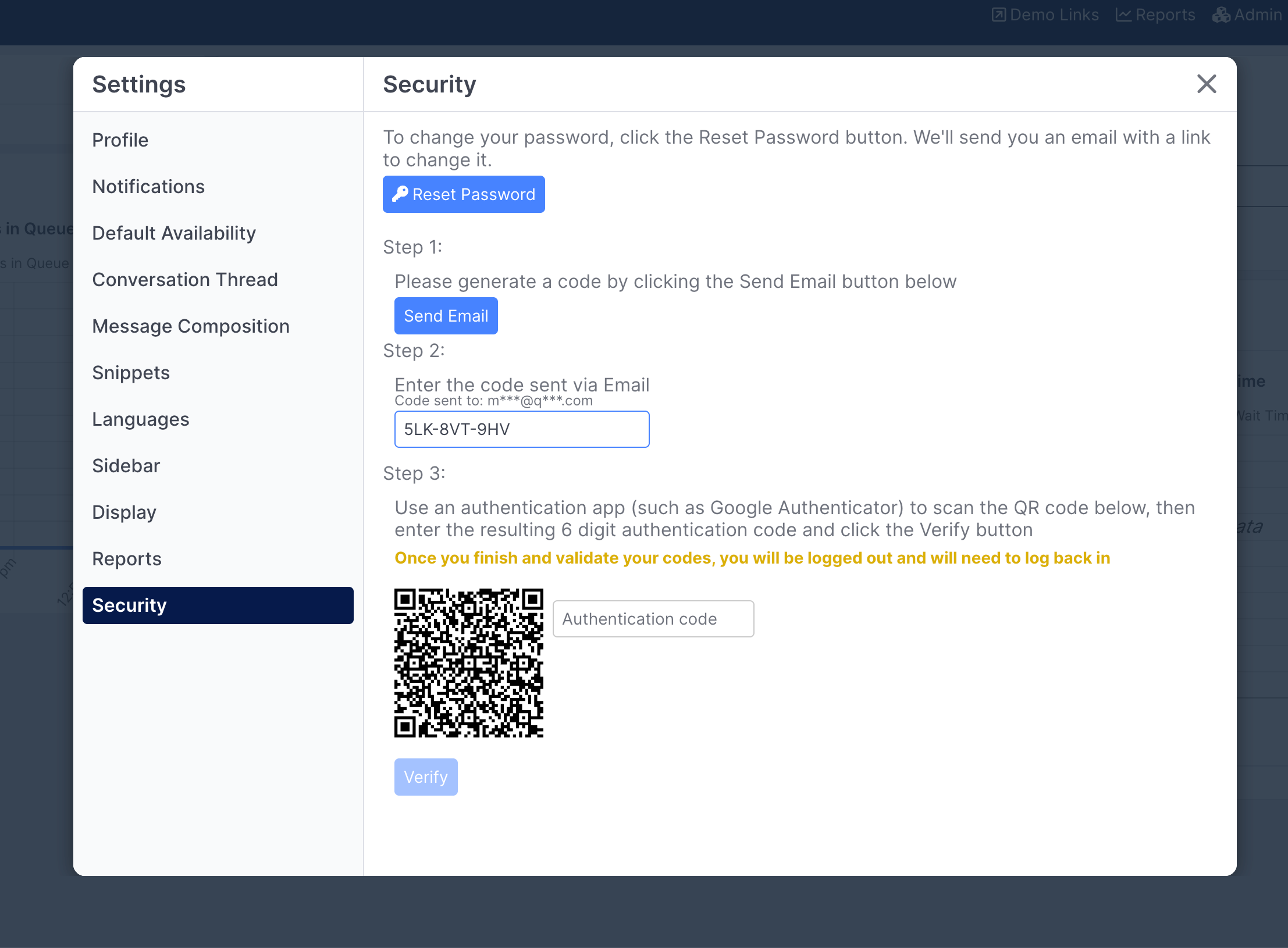
Once that code is scanned, you've entered your authentication code, and you've clicked Verify, you will be logged out and can then log back in using 2FA:
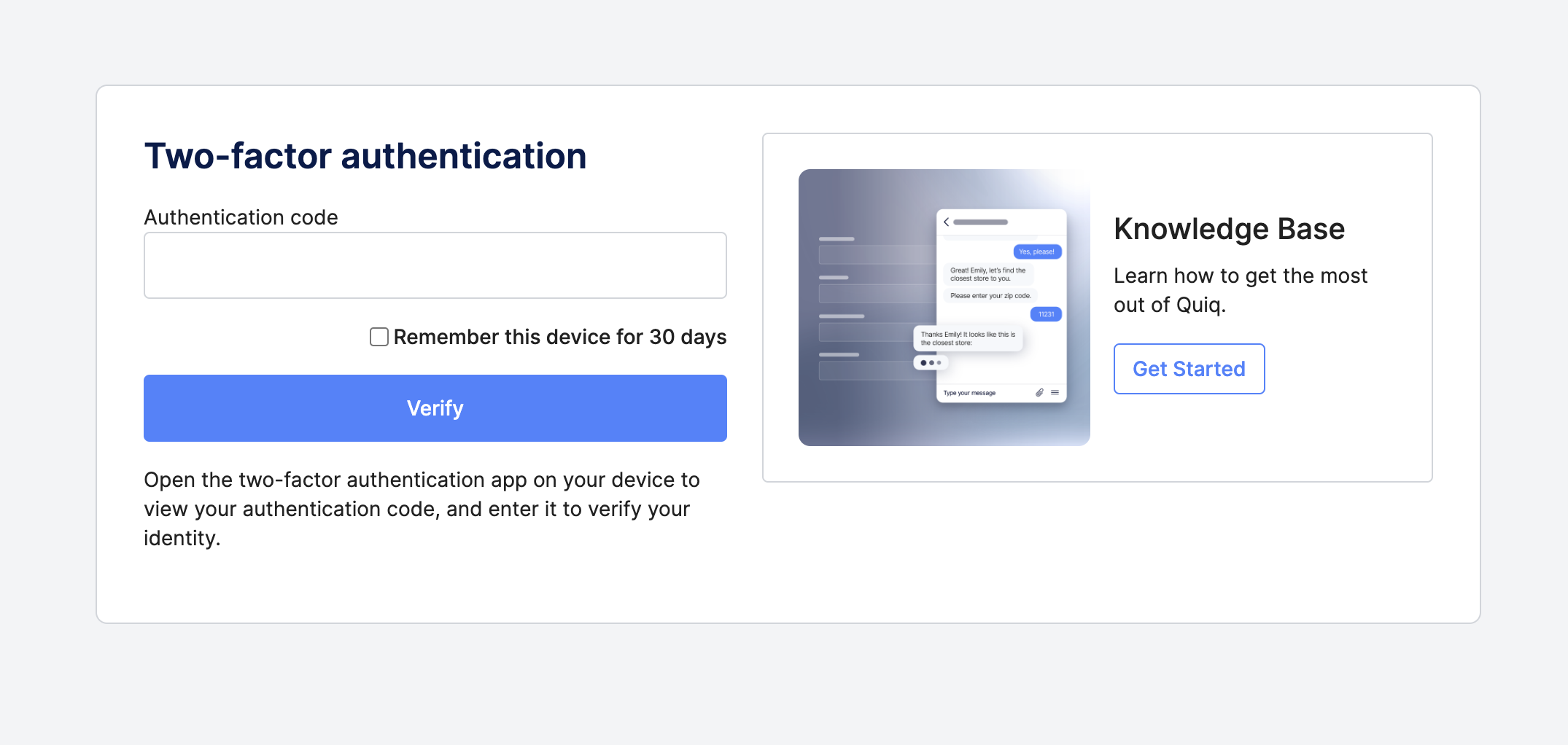
After you've logged back in, you'll be taken back to the Security page, where you can now enable 2FA for your entire organization.
Two-Factor Authentication Rollout
Users will receive the following popup when 2FA is turned on for the first time, which will require them to scan the QR code with their Time-based One-Time Password (TOTP) app, and enter the 6 digit authentication code:
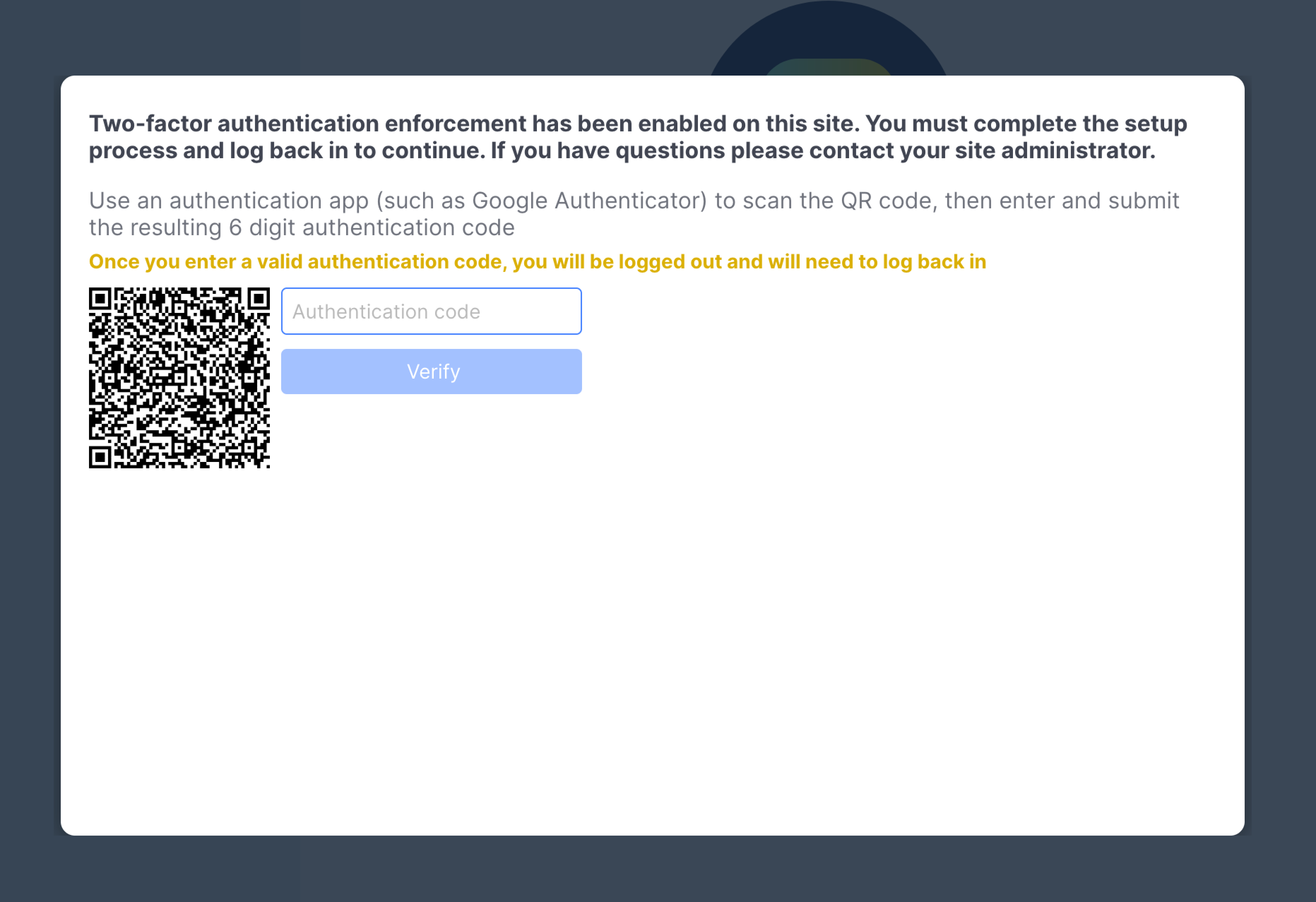
Agents with Active ConversationsAgents with active conversations will not automatically be logged out and taken away from their current conversations when 2FA is turned on.
They will be logged out once their session refreshes and they'll need to go through the 2FA flow. Session refresh can happen at any time within a 5 minute interval, so it's best to enable 2FA when volume is low, or outside of business hours.
Time-based One-Time Password (TOTP) or Authenticator AppsThere are a range of Time-based One-Time Password (TOTP), more commonly know as authentication apps, users can use, such as Google Authenticator (Apple App Store download link, Google Play Store download link). Users will need to download an authenticator app on their mobile device in order to complete 2FA.
Once users have successfully entered their authentication code, they'll be logged out of Quiq and prompted to log in again using their existing credentials & an authentication code:
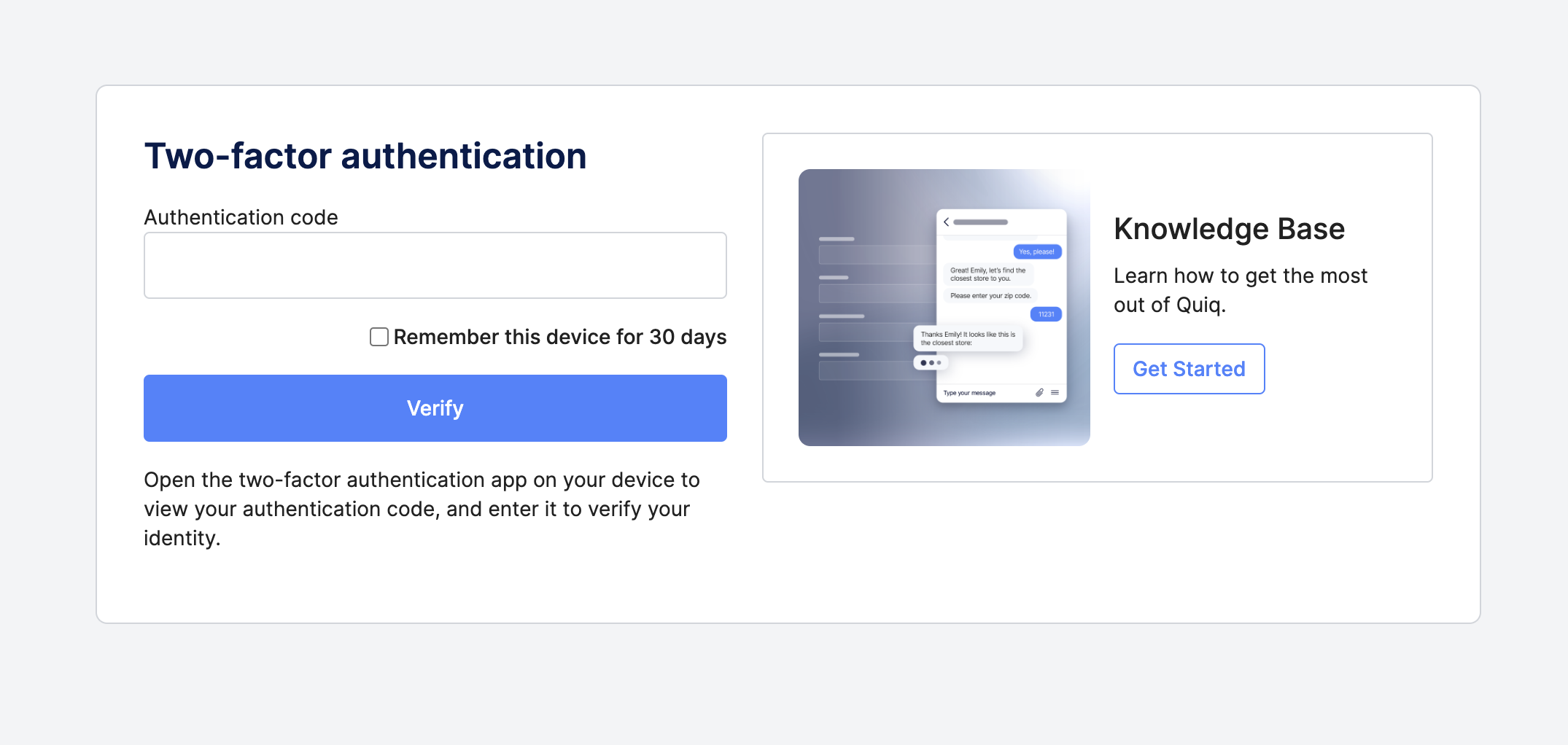
From there, they can continue to use Quiq as normal, and will now have Two-Factor Authentication as part of their login flow whenever they need to login to Quiq again.
Frequently Asked Questions
We don't use Quiq as our Identity Provider (IdP), do we still need to enable 2FA within Quiq?
No, if your users are not signing into Quiq directly, but are using Salesforce, Oracle, or any other IdP, you do not need to enable 2FA within Quiq. However, you must have 2FA enabled in your own IdP if you're not using Quiq.
Will every user in my organization need to use 2FA?
Yes, every user, regardless of permission level, with a Quiq account will need to have 2FA enabled in order to login.
What methods of 2FA do you support?
Quiq supports 2FA via an Authenticator app.
Will all users in my Tenant by logged out immediately when I enable 2FA?
Users will not be logged out immediately when 2FA is enabled, however they will be logged out once their session refreshes, which will generally happen within 5 minutes of enabling 2FA. It's best to communicate this change to your organization and turn it on when volume is low, or outside of business hours to minimize impact to your customers and any in flight conversations you may be having.
Questions and Concerns
If you have questions or concerns, please reach out to [email protected]
Updated 1 day ago
